When a data breach occurs, and you have to tell your shareholders or customers that business-sensitive information or their personal information may have been compromised by one of your third-party vendors, nobody is going to look at the third-party vendor — they’ll be looking at the primary organization that was entrusted to protect the data and manage third-party risk appropriately.
A data breach often involves significant amounts of time, resources, and cost to fix a problem caused by a third-party risk that was not managed. However, regardless of how much you clean things up, no remediations will stop the reputational damage that will continue to cost your organization in lost business.
You cannot ignore the potential consequences of properly managing third-party risk.
Read our blog post, “How Can Generative AI Be Used in Cybersecurity?”
The "risk" of not managing third-party vendor cyber risk
In addition to managing third-party vendor risk and maintaining customer trust, cyber insurance is becoming necessary. Meanwhile, insurance premiums are increasing annually as the risk of cyber-attacks and the costs associated with a data breach increase. Effective third-party vendor risk management could make the difference between the cost of your premiums or insurers deeming your organization ineligible for coverage.
According to the global IBM Data Breach Report for 2022:
- The average cost of a data breach in the U.S. is $9.44M
- For 83% of companies, it’s not a matter of whether a data breach will occur but when and how prepared they will be to deal with such an event.
With today’s increasing integration of applications and interfaces between your organization and your third-party vendor, all aspects of cybersecurity hygiene come into play as your third-party vendor risks become your organizational risks.
There needs to be an examination of the multiple layers of third-party vendors with traceability and accountability at each level for cybersecurity and privacy practices that may impact your organization’s overall security and ability to fulfill regulatory compliance laws.
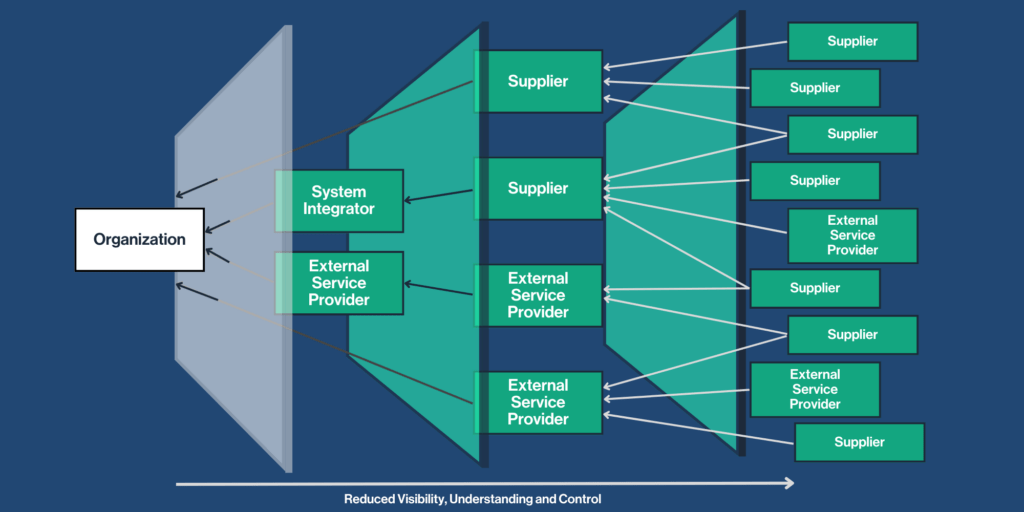
Third-party vendor risk management is critical to a solid cybersecurity and privacy program in both the public and private sectors.
The Department of Energy (DOE) has developed a concise Cybersecurity Capability Maturity Model for the Energy Sector C2M2 v2.1 June 2022, which spells out in several sections the importance of reviewing your third-party vendor’s cybersecurity practices. This process includes assessments of their third-party vendors’ security practices.
The Federal Trade Commission (FTC) cautions organizations that contract third-party vendors to manage sensitive personal data and security practices that should be in place.
The Cybersecurity and Infrastructure Security Agency (CISA) developed a Cyber Resource Hub to provide multiple resources to help the public and private sectors assess risk and their security processes, which can help manage third-party vendors.
Tips to lower your risk of third-party vendor risk management
One of the best ways to prevent a data breach is to understand why it would happen.
Malicious actors can have several motivating factors for breaking into an organization. Those factors could be financially or politically motivated, or the malicious actor is seeking vindication or plain old bragging rights among the hacker community. These motivating factors can help you understand why your organization may be a target.
Malicious actors may not always try to attack your organization head-on; they may go in through your employees, guests, or third-party vendors — whatever is the easiest method.
Below are some essential tips to help your organization manage third-party vendor risk and the best practices associated with each.
- Assess your third-party vendors’ security posture. Understand both their security and privacy program through an assessment. Understand what frameworks and security maturity model(s) their security and privacy programs are aligned with and their vulnerability management process, which could include external audits, certifications, and scanning. Request documented evidence regarding audit reports, security assessment certifications, or vulnerability remediations.
- Educate on compliance requirements. Ensure your third-party vendors thoroughly understand any global regulatory compliance laws and requirements your organization must comply with and any cascading requirements the third party needs to align with. Sharing these requirements with your third-party vendor will help your organization and benefit the third party in marketing their ability to support such global requirements.
- Employee awareness. People are often the weakest link in most organizations and one of the top causes of data breaches through poor security practices, phishing attacks, or a general lack of training on security best practices. Ensure that both your organization and your third-party employees are regularly training and testing on security and privacy best practices and appropriate actions to take.
- Collaborate regularly. Collaborate with your third-party vendors’ security teams to understand the shared risks, changing threat landscape, intel, and best practices. Having ongoing transparent dialogue will help your organization and third-party vendor organization increase their security postures, which is ultimately the goal of all security departments.
- Stay in touch. Vendor risk management is not a one-time activity; at least annually, there needs to be consistent monitoring. There may be changes in the third-party vendor’s security and privacy program and posture that your organization needs to be aware of, and your organization may need to communicate any changes in security requirements that your third-party vendor will need to support.
One of the best ways to manage third-party vendor risk is to understand your organizational and third-party risks and what factors would play into either organization being attacked.
We recently hosted a cybersecurity webinar for public power utilities: “Evolving Cybersecurity Threats & Challenges to Public Power.” Request the slides for this webinar and find more information in an additional blog post: “Can You Spot a Cyberattack?“